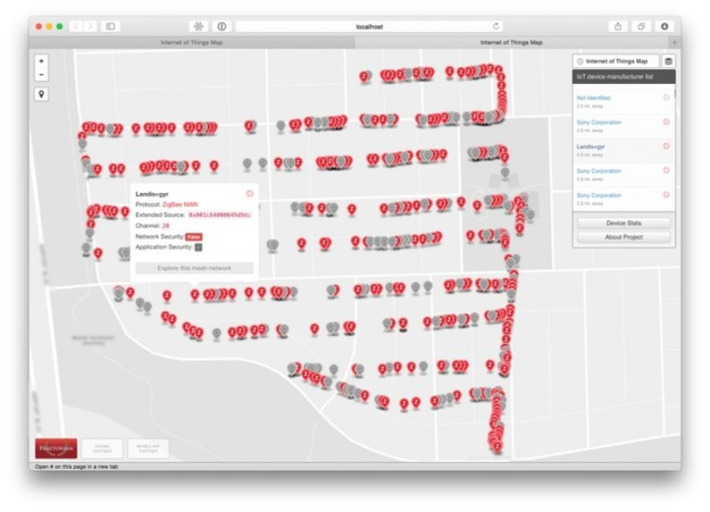
Early this year the staff at Epicenter, a Stockholm based high-tech company, were given a choice; they could either be issued a standard employee ID card for access to the building and office equipment, or they could be injected with a tiny radio frequency identification device, placed just under the skin of their hand – otherwise known as a subcutaneous implant. Surprisingly, a number chose the chip, on the promise that with a wave of their hand they would be able to access the building, open doors, operate photocopiers and even pay for lunch in the company cafeteria. No ID cards to forget at home or passwords to remember.
In fact, the Epicenter case is hardly the first experiment of its kind. Going back as far as 2004, Barcelona nightclub owner Conrad Chase offered RFID chipping to his VIP clients enabling access to special lounges and payment capability.
Via André Bélanger, Farid Mheir



 Your new post is loading...
Your new post is loading...

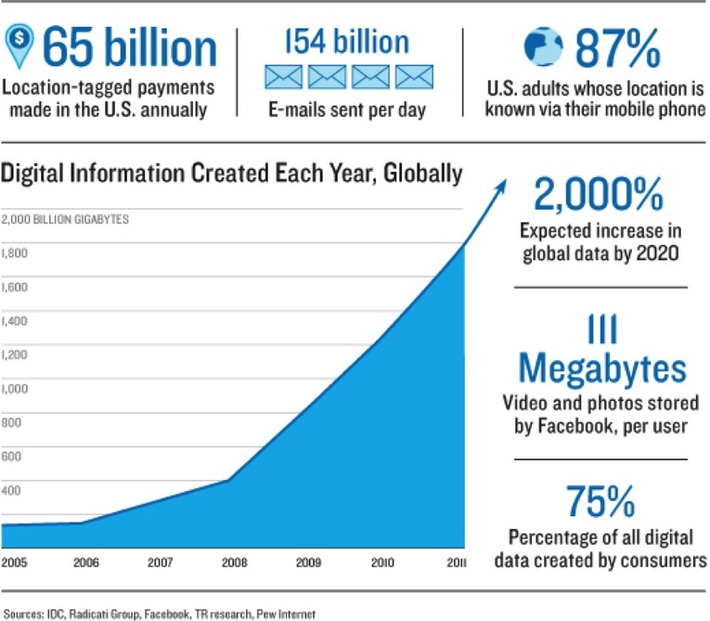






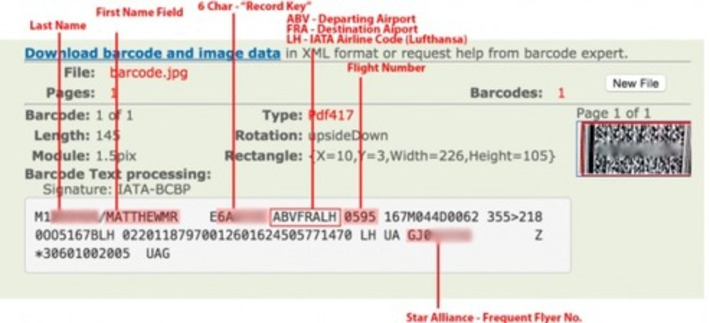





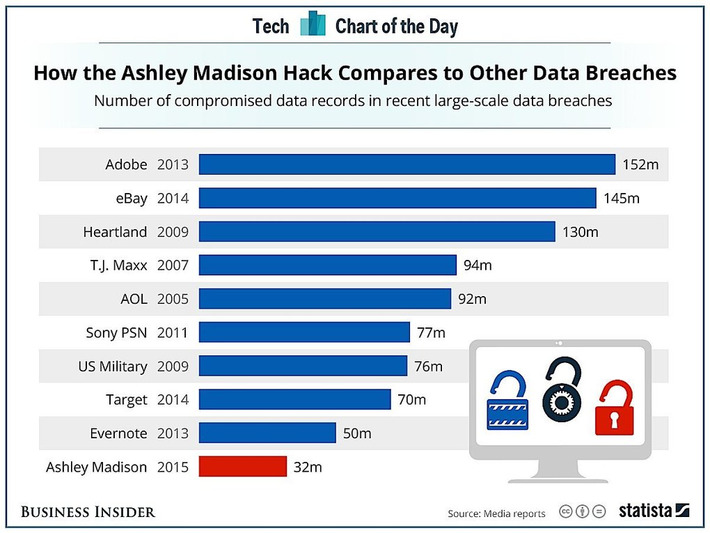
















I knew they did this for dogs but never thought they did it for humans. But come to think of it, makes perfect sense. Or it will become the biggest invasion of privacy ever.
Great insight from André!