A discovery about Facebook's official Android app once again puts into question if the social network's developers truly *get* security and privacy.
As Symantec describe on its blog, when its developers tested its new Norton Mobile Security product against some of the world’s most popular Android apps, they were disturbed to see a warning message claiming that the Facebook Android app leaks personal information without the device owner’s knowledge:



 Your new post is loading...
Your new post is loading...







![Managing Mobile Privacy | Security Intelligence Blog [Infographic] | 21st Century Learning and Teaching | Scoop.it](https://img.scoop.it/m8EBNAOuN5Zr7PdORj8fTDl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)

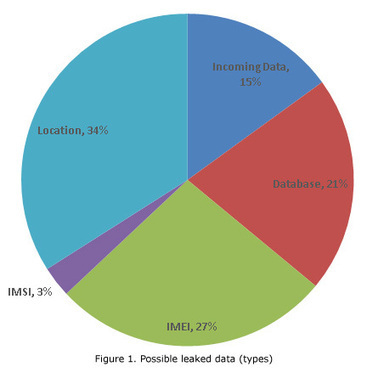






As Symantec describe on its blog, when its developers tested its new Norton Mobile Security product against some of the world’s most popular Android apps, they were disturbed to see a warning message claiming that the Facebook Android app leaks personal information without the device owner’s knowledge...
Beware Andriod users! Will a vpn protect your info?