A shake-up is coming to the mobile security industry, and it will happen when Google begins to secure its Android environment, David Duncan, CMO of Webroot, says.
When you look at most of the mobile apps, you accept the application and its privileges settings, and there is very little ability for you to customise those settings, so you either agree or disagree.
App developers are trying to monetise their apps, because remember, most of these are being sold for $1.99 or they're free, so the only way that they are going to make money is collecting and harvesting data, and selling it to a data house, who in turn is going to sell it to advertisers.
Learn more:
- http://www.scoop.it/t/apps-for-any-use-mostly-for-education-and-free



 Your new post is loading...
Your new post is loading...



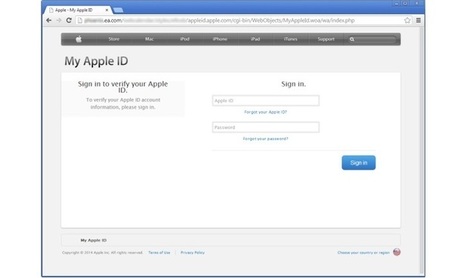





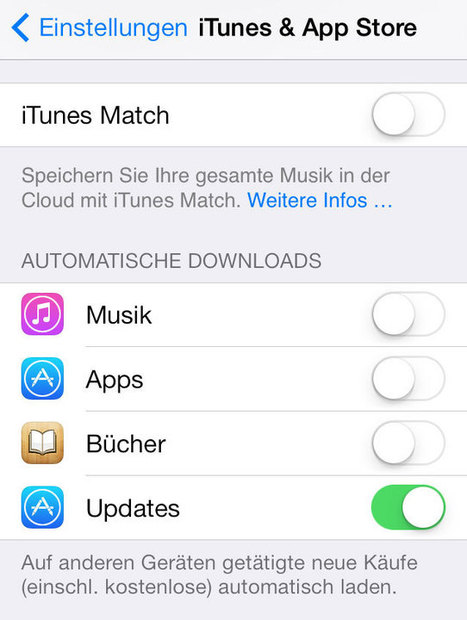

![BYOD Security Issues [Infographic] | 21st Century Learning and Teaching | Scoop.it](https://img.scoop.it/CaiNaHRcRGZDVZM2V3tufTl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)








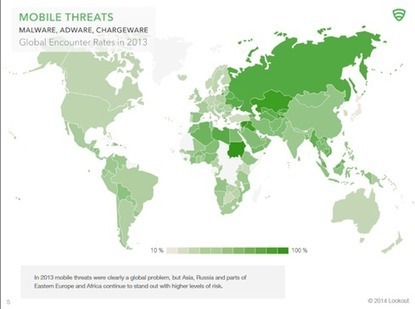


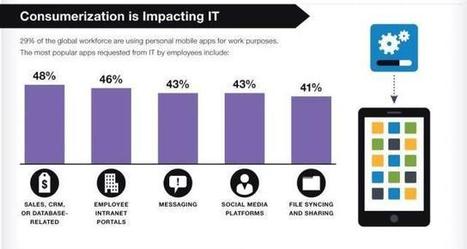





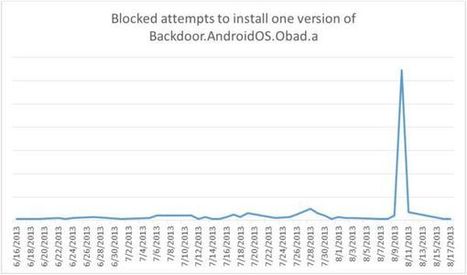
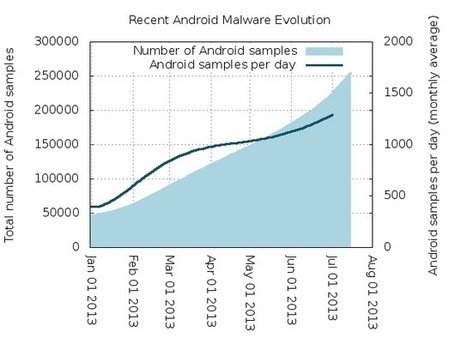





When you look at most of the mobile apps, you accept the application and its privileges settings, and there is very little ability for you to customise those settings, so you either agree or disagree.
App developers are trying to monetise their apps, because remember, most of these are being sold for $1.99 or they're free, so the only way that they are going to make money is collecting and harvesting data, and selling it to a data house, who in turn is going to sell it to advertisers.
Learn more:
- http://gustmees.wordpress.com/2014/03/05/often-asked-questions-are-there-cyber-security-dangers-with-apps-and-whats-about-privacy/
- http://www.scoop.it/t/apps-for-any-use-mostly-for-education-and-free