Parler lacked the most basic security measures that would have prevented the automated scraping of the site's data. It even ordered its posts by number in the site's URLs, so that anyone could have easily, programmatically downloaded the site's millions of posts. Parler's cardinal security sin is known as an insecure direct object reference,
Research and publish the best content.
Get Started for FREE
Sign up with Facebook Sign up with X
I don't have a Facebook or a X account
Already have an account: Login
Get weekly or monthly digest of all posts in your inbox: https://fmcs.digital/wim-subscribe
Curated by
Farid Mheir
 Your new post is loading... Your new post is loading...

Martin (Marty) Smith's curator insight,
December 19, 2018 8:15 AM
Meeker is as close to Nostradamus as we are likely to get.

Кирилл Беличенко's curator insight,
November 30, 2022 6:42 AM
Zagrożenia internetowe i statystyki hakerskie
GigWriting.com's curator insight,
November 25, 2017 8:10 AM
Article to be referred by every web-designers and website owners. Thanks - Gigwriting.com

Кирилл Беличенко's curator insight,
November 30, 2022 6:44 AM
Statystyki włamań do stron internetowych i kradzieży danych

Jean-Marie Grange's comment,
December 20, 2016 1:12 PM
Maybe one solution would be for content publishers to offer the choice of paying a fair amount for ad-free content... http://sco.lt/7CrAVl
|

Curated by Farid Mheir
Get every post weekly in your inbox by registering here: http://fmcs.digital/newsletter-signup/
|




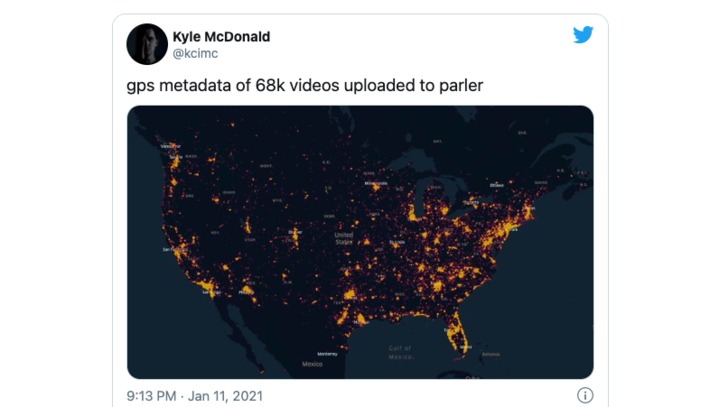




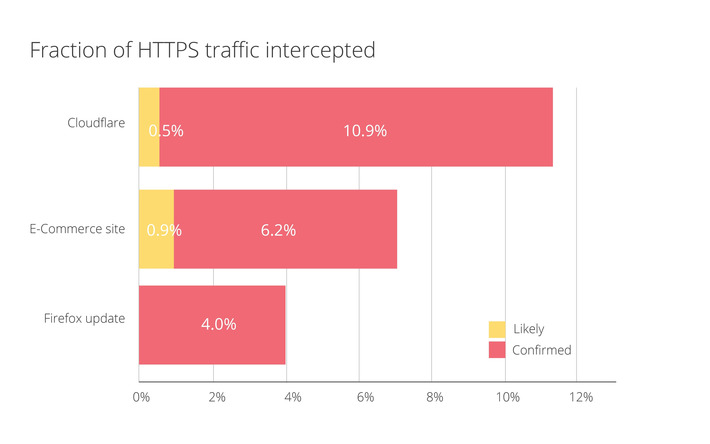












WHY IT MATTERS: security has become central in our age of digital transformation. Yet, it seems, most people are either unaware of basic security principles, or not willing to invest time or money to do it. And I am not even talking of doing it *well*. Just implementing proper security measure. In this case it affect Parler, which in itself I don't much care about (they deserve it for such a stupid mistake). But their lack of security impacts their users privacy as well. And that includes potentially millions of people (in the photo, 68000 video have been geolocated - too bad for keeping your anonymity ;-)