Last month’s story about organizations exposing passwords and other sensitive data via collaborative online spaces at Trello.com only scratched the surface of the problem. A deeper dive suggests a large number of government agencies, marketing firms, healthcare organizations and IT support companies are publishing credentials via public Trello boards that quickly get indexed by the major search engines.
Research and publish the best content.
Get Started for FREE
Sign up with Facebook Sign up with X
I don't have a Facebook or a X account
Already have an account: Login
Get weekly or monthly digest of all posts in your inbox: https://fmcs.digital/wim-subscribe
Curated by
Farid Mheir
 Your new post is loading... Your new post is loading...
|

Curated by Farid Mheir
Get every post weekly in your inbox by registering here: http://fmcs.digital/newsletter-signup/
|




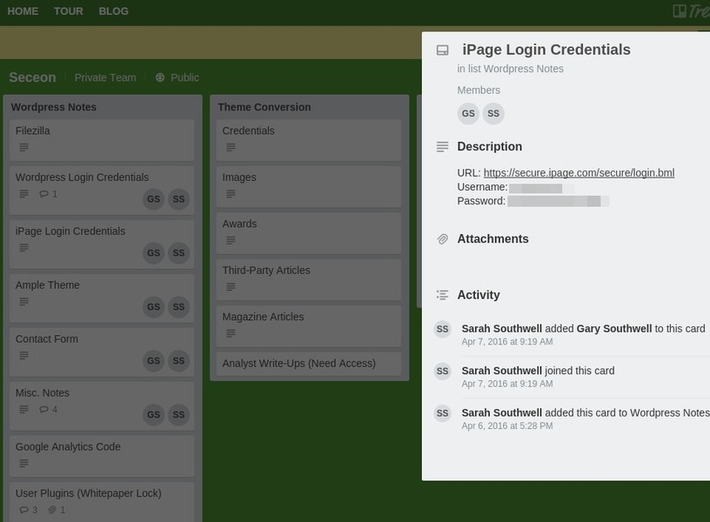









WHY IT MATTERS: this article is a reminder that the use of public software as a service tools may lead to exposure of critical and private corporate data. In the past, locking everything down behind corporate firewall and network meant this was not possible. At the same time, remote work and collaboration with partners around the globe was very difficult. CIOs would like to return to the good old days but users certainly do not want that. Proper governance must be enforced with these new tools and systems.