Download the report to find out:
- How big tech companies are looking to gain from quantum advances and their strategies for commercializing quantum computing
- The different approaches they are using to develop their own quantum computers
- How big tech giants are using partnerships to build out their quantum capabilities and stake out market positions
- Which strengths and capabilities differentiate each big tech company in quantum



 Your new post is loading...
Your new post is loading...

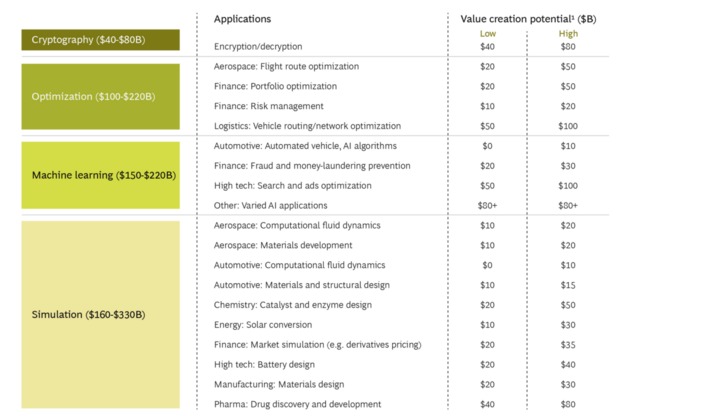





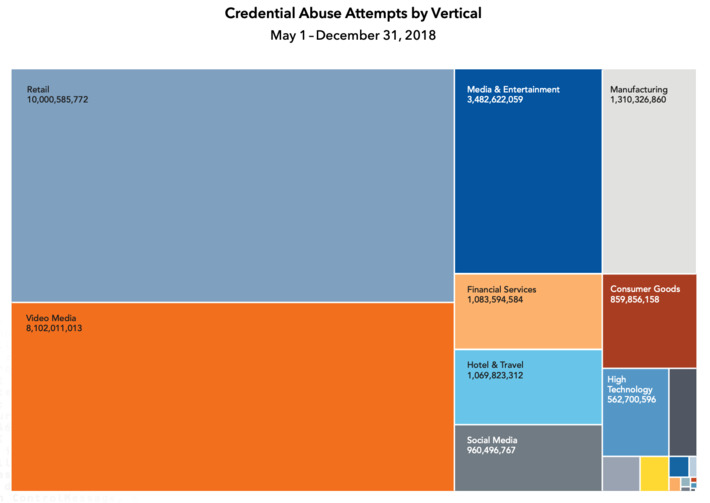
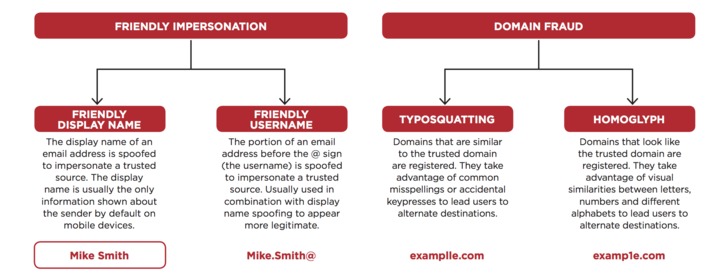

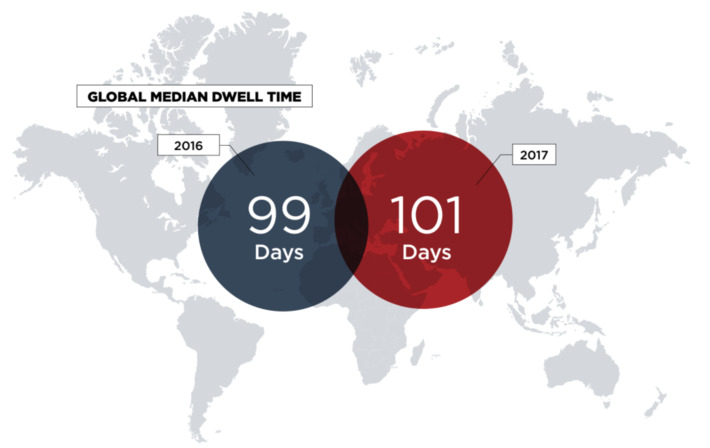
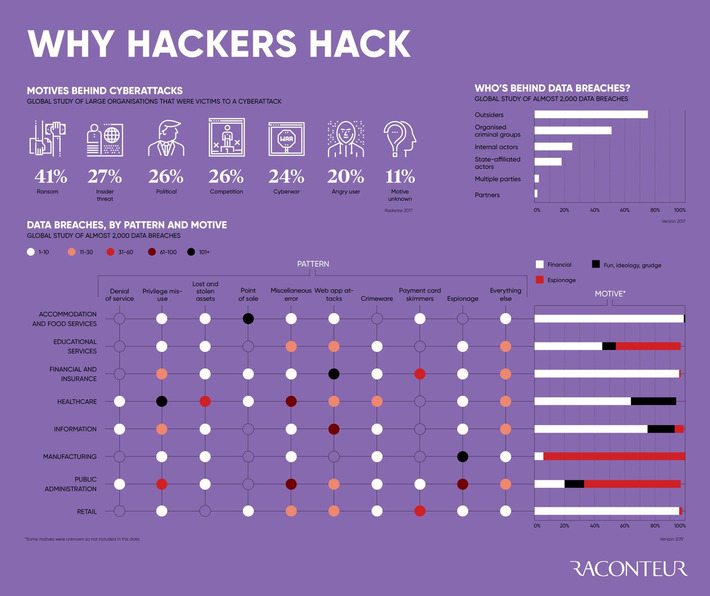

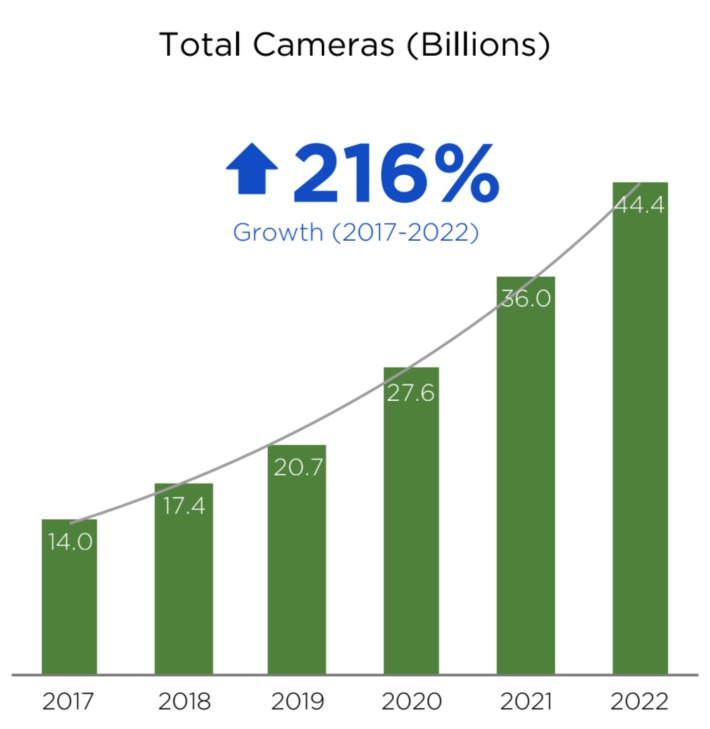
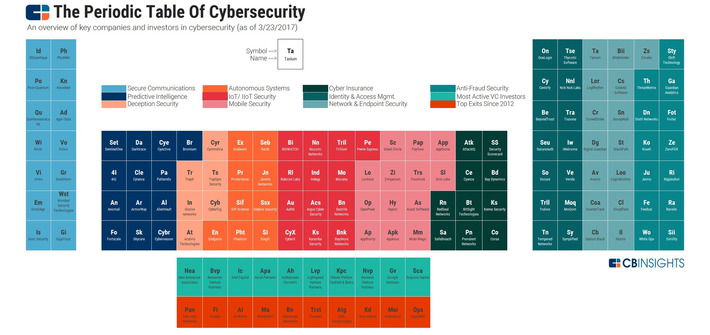

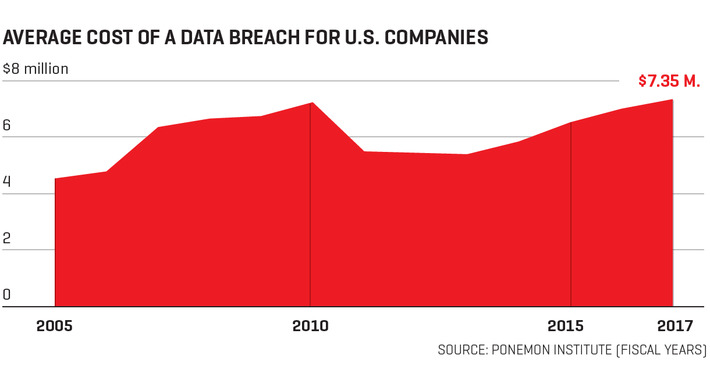











WHY IT MATTERS: quantum computing commercial applications is far in the future. But I found this paper from CBinsights useful as it highlights the many possible applications beyond cryptography.