How to get off of people search sites like Pipl, Spokeo, and WhitePages.
Research and publish the best content.
Get Started for FREE
Sign up with Facebook Sign up with X
I don't have a Facebook or a X account
Already have an account: Login
Get weekly or monthly digest of all posts in your inbox: https://fmcs.digital/wim-subscribe
Curated by
Farid Mheir
 Your new post is loading... Your new post is loading...

Don Sadiri Daquitan Quia-eo's curator insight,
February 20, 2019 8:09 PM
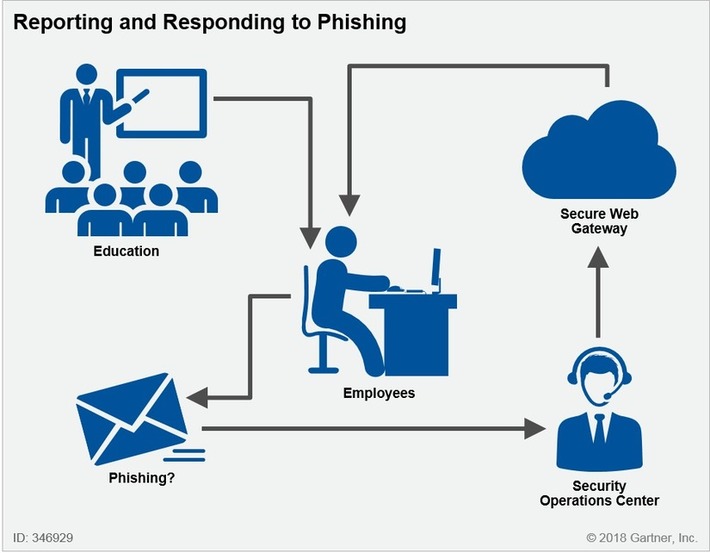
Phishing is a crime (cybercrime) where the criminals poses as someone. They would somehow create a poser account or they would create a fake website where the victims would log in and then their account would immediately appear to the criminals. Financial loss and stealing of other important documents or things are often the outcome of phishing crime. So, in order to avoid these incidents we need to check everything twice or thrice. For example, check the url of the website if it is legitimate like there would be "www" and "https", it means that the site you are using is SECURED.

Honnie Faith Balingway II's curator insight,
February 20, 2019 10:03 PM
(My knowledge about computer networking basics)
From my knowledge, Computer networking is part of my knowledge as an i.c.t student and i konw that computer networking is as a group of two or more computer systems or other devices that are linked together to exchange data. There are many types of computer networks. Common types of networks include the following: The Local Area Network, Wide-area network, Metropolitan-area network,Home-area network, Virtual private network and Storage area network. Networks share common devices and functions, such as servers, transmission media (the cabling used to connect the network) clients, shared data (e.g. files and email), network cards, printers and other peripheral devices. And an important relationship on networks is that of the server and the client. 
Edward Dimaden's curator insight,
February 21, 2019 2:16 AM
their are many things in this world that they going to attacks some person for block mail and this issue is gonna be stop
we us young people start to defense this issue, we united as one so stop cyber-attacks.

Vezta & Co.'s curator insight,
September 29, 2018 11:27 AM
WHY IT MATTERS: this new service will help you determine if your account has been hacked and watch for it. This is a new twist on a service I discussed before http://fmcs.digital/?s=pwned but that remains more valuable than ever today.

Ocean´s five's curator insight,
October 31, 2017 6:44 AM
Las 140 startup de la tabla periódica. Así son las empresas que definen la industria de seguridad cibernética. Entre las categorías se encuentran:
-Seguridad móvil: Zimperium y Appthority. -Cyber Insurance: RedSeal Networks y Cyence. -Administración de identidad y acceso: OneLogin. -Seguridad de red y punto final: Tanium, Cloudflare , Illumio y Zscaler . -Seguridad contra el fraude:ThreatMetrix.

Jean-Marie Grange's comment,
December 20, 2016 1:12 PM
Maybe one solution would be for content publishers to offer the choice of paying a fair amount for ad-free content... http://sco.lt/7CrAVl
|

Curated by Farid Mheir
Get every post weekly in your inbox by registering here: http://fmcs.digital/newsletter-signup/
|










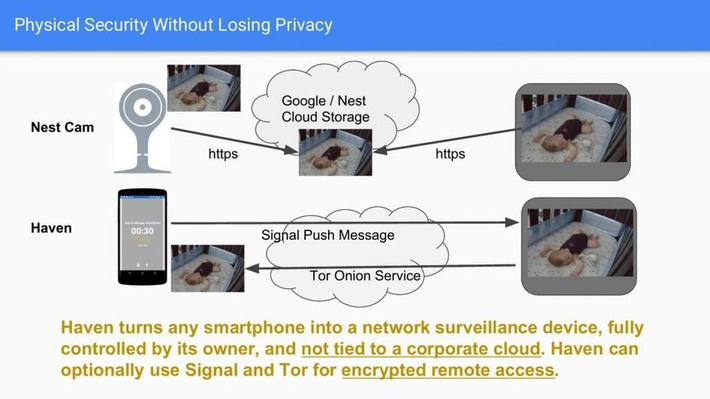
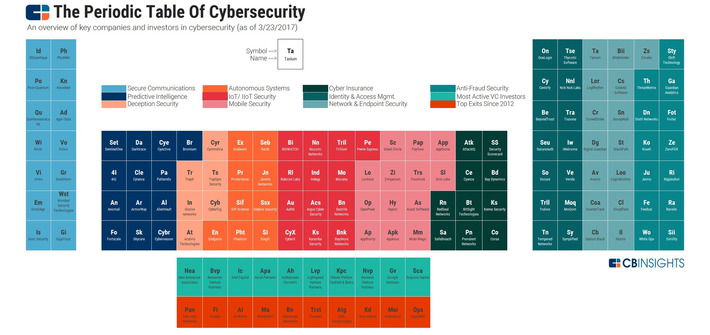

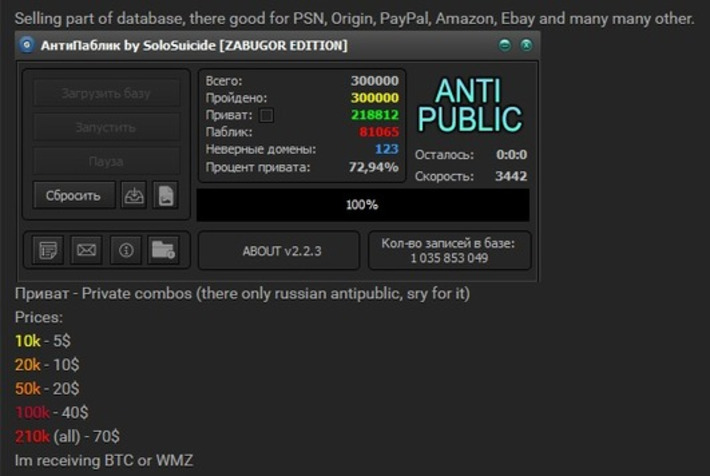

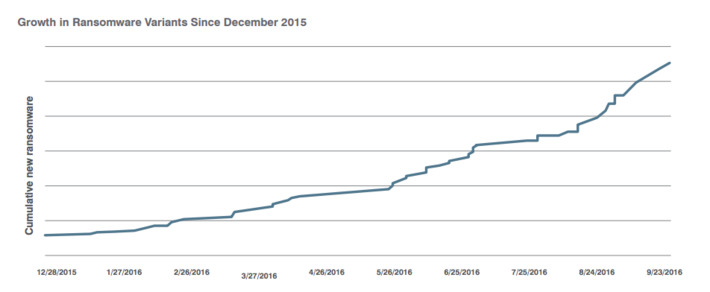




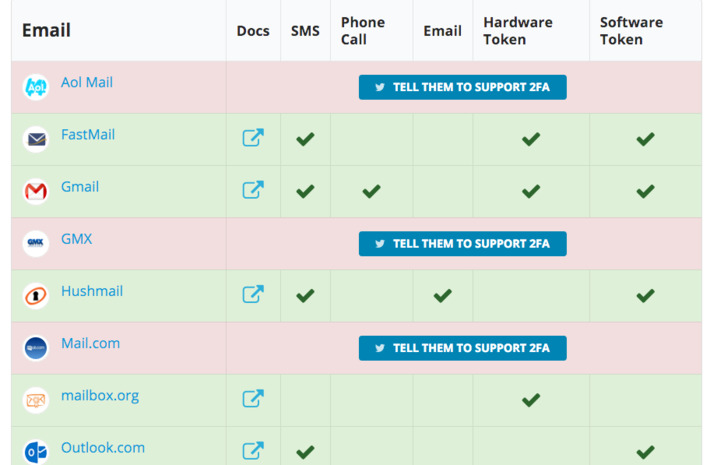








WHY IT MATTERS: protecting privacy is a difficult task, sometimes an impossible one. Case in point this long list of sites you have to go through to opt-out or delete your data. We need a better solution...