The best protection against being hacked is well-informed developers. Make your development team into security experts today.
Research and publish the best content.
Get Started for FREE
Sign up with Facebook Sign up with X
I don't have a Facebook or a X account
Already have an account: Login
Get weekly or monthly digest of all posts in your inbox: https://fmcs.digital/wim-subscribe
Curated by
Farid Mheir
 Your new post is loading... Your new post is loading...
|

Curated by Farid Mheir
Get every post weekly in your inbox by registering here: http://fmcs.digital/newsletter-signup/
|




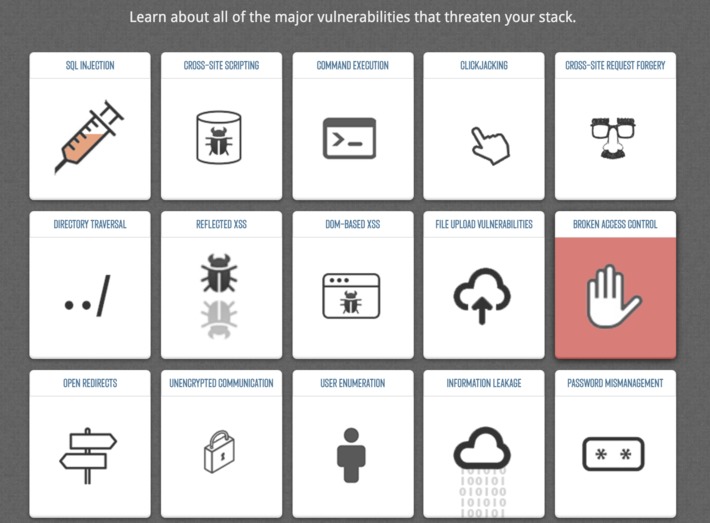

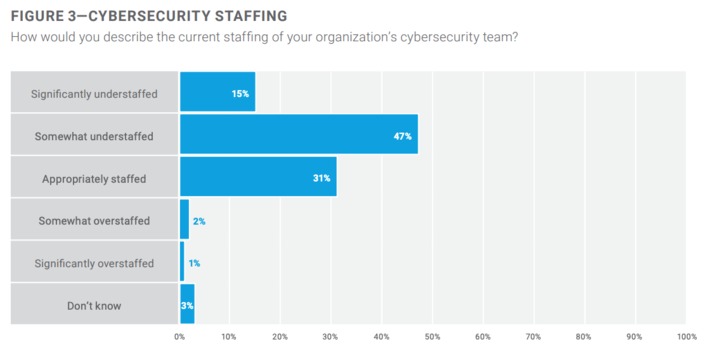

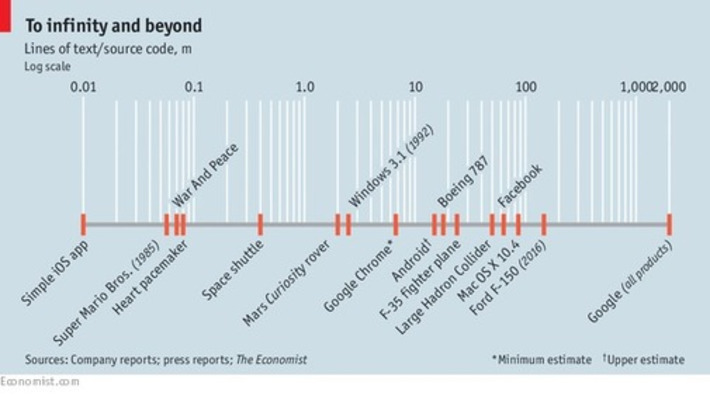









WHY IT MATTERS: amazing reference to understand the most common hacks in digital: SQL injection, cross-site scripting and many more. A reference to bookmark.