A billion people in the world have no legal identity. Without an ID they can’t open a bank account, get a loan, or even vote. Now a tech entrepreneur has come up with an answer.
Research and publish the best content.
Get Started for FREE
Sign up with Facebook Sign up with X
I don't have a Facebook or a X account
Already have an account: Login
Get weekly or monthly digest of all posts in your inbox: https://fmcs.digital/wim-subscribe
Curated by
Farid Mheir
 Your new post is loading... Your new post is loading...
Tracy Harding's comment,
September 1, 2015 9:19 AM
You need to work on formatting of your replies. This is one giant sentence. Remember the requirements. You need a 2-3 sentence summary, at least 1 sentence of IR implications and 1 sentence about your thoughts.

Farid Mheir's comment,
September 1, 2015 9:23 AM
@Tracy Harding: not sure I understand your comment re: formatting. Can you be more specific and email me a screengrab? thank you!
|

Curated by Farid Mheir
Get every post weekly in your inbox by registering here: http://fmcs.digital/newsletter-signup/
|




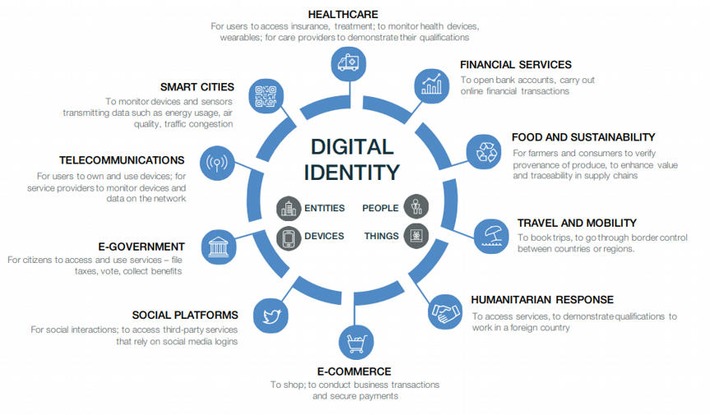

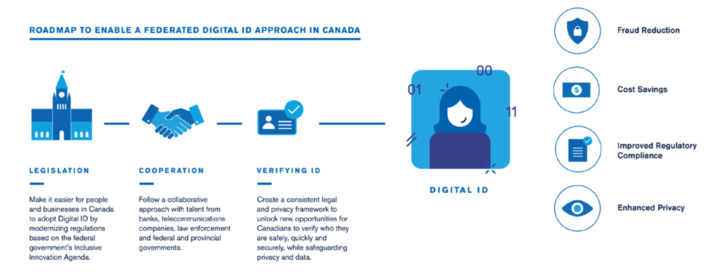
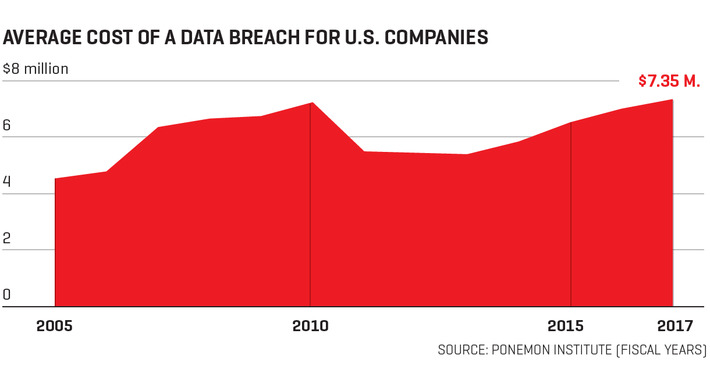

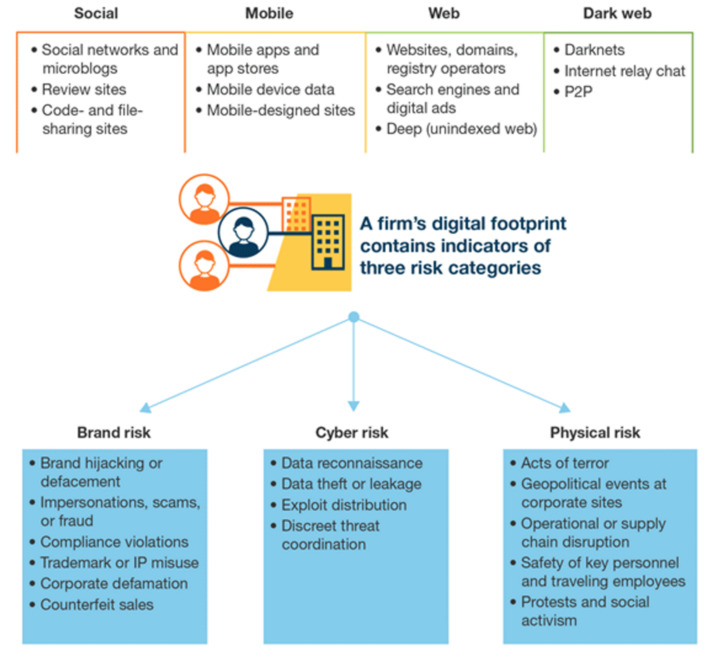
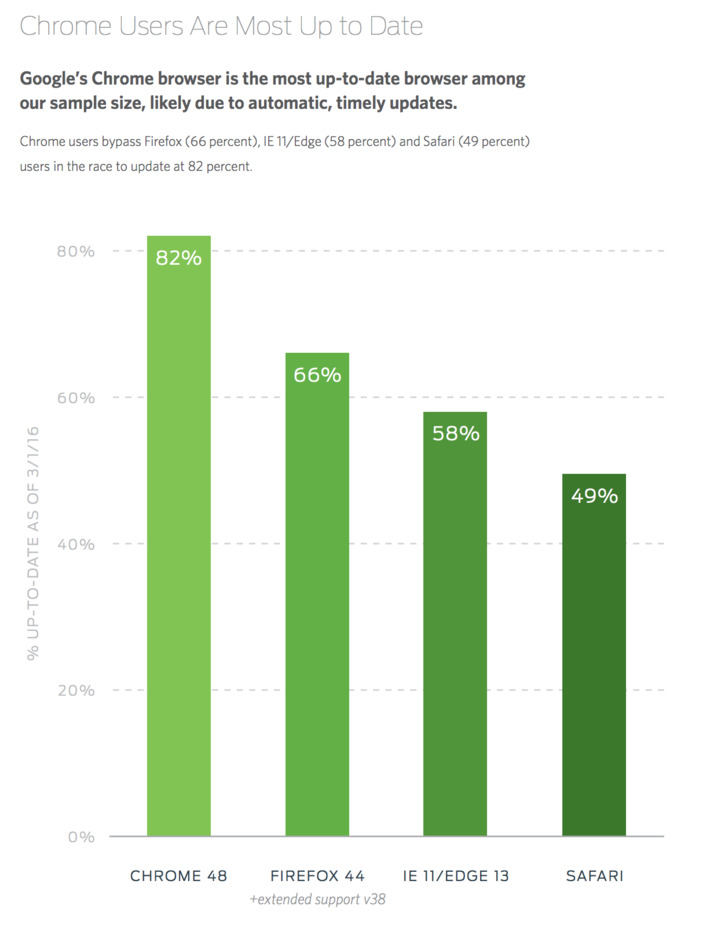
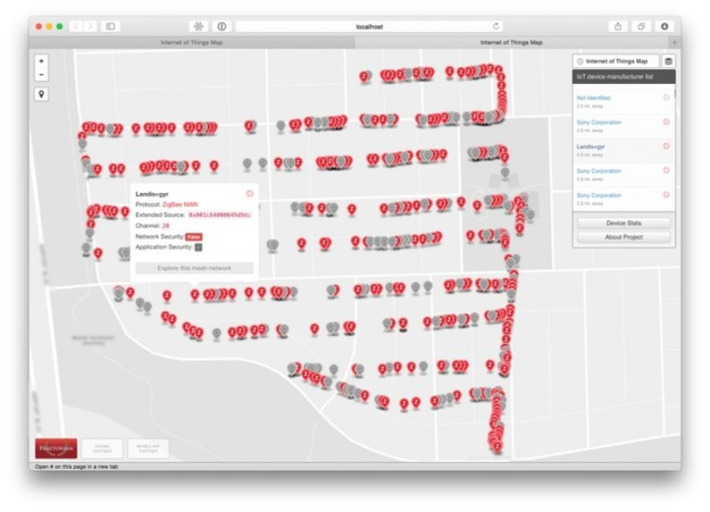








WHY IT MATTERS: an amazing article from WEF about how important digital identity is. The diagram is also a great summary of the potential use cases for digital IDs. In short: its way more than a digital version of your passport.