5 key recommendations
- Don’t reject BYOD — be prepared for it. Give your IT administrators actionable data on device ownership and health that can inform risk-based access control decisions.
- Encourage safe computing practices and good security hygiene, such as running regular security updates or using device encryption, passcodes and additional authentication to protect systems and data.
- Configure systems and deploy policies that enable automatic updates for as much software as possible to remove some of the friction that users feel when manually installing updates. We found that an overwhelming number of out-of-date browsers and systems don’t take basic steps like enabling automatic updates.
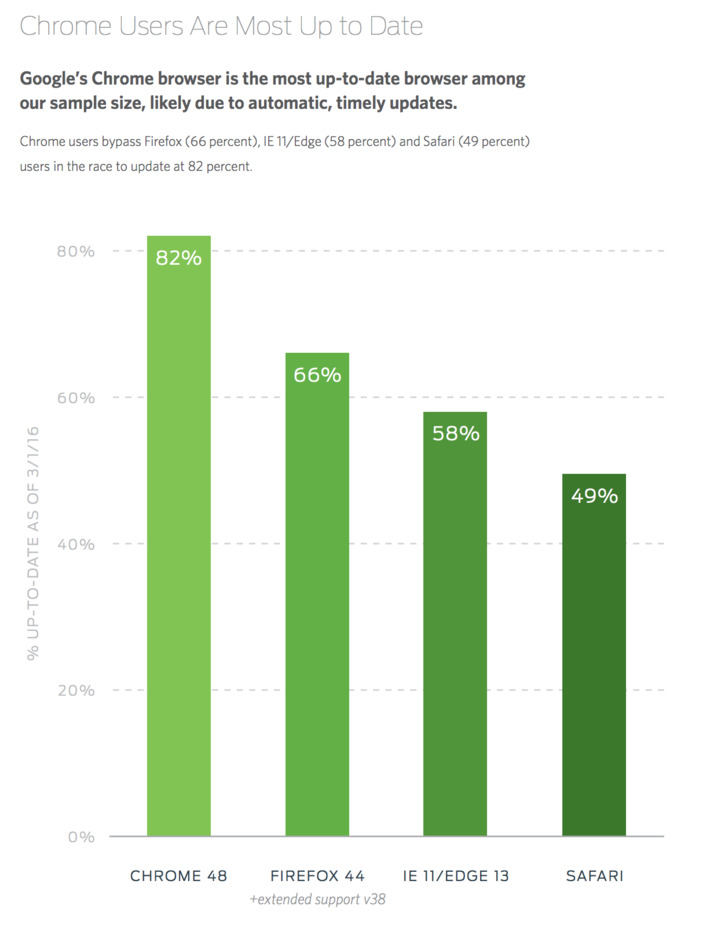
- Switch to browser platforms that update more frequently and automatically, like Google Chrome.
- Disable Java and prevent Flash from running automatically on corporate devices, and enforce this on user-owned devices through endpoint access policies and controls.



 Your new post is loading...
Your new post is loading...











DUO security publishes a report on security findings from over 2M devices its software is installed on and provides recommendations from its findings
WHY THIS IS IMPORTANT
Security is better, it seems, when users use software that update themselves automatically. Unfortunately, because enterprises have to pay to keep software up to date, most computers are out of date from a security standpoint. Leaders should prioritize keeping systems up to date or favour solutions with automated and free updates. As the paper describes, there are many out there, you just have to look for them carefully.