Internet infrastructure giant Akamai last week released a special State of the Internet report. Normally, the quarterly accounting of noteworthy changes in distributed denial-of-service (DDoS) attacks doesn’t delve into attacks on specific customers. But this latest Akamai report makes an exception in describing in great detail the record-sized attack against KrebsOnSecurity.com in September, the largest such assault it has ever mitigated.
Get Started for FREE
Sign up with Facebook Sign up with X
I don't have a Facebook or a X account
 Your new post is loading... Your new post is loading...

Farid Mheir's curator insight,
March 15, 2016 8:33 AM
An old Wired magazine article from 2012 that is still as current today as it was then. Unfortunately.
If you don't read the whole thing, just skip to the DOs and DONTs. And read these other articles: http://www.scoop.it/t/digital-transformation-of-businesses/?tag=Security 
jasmine moriah gabrielle hummel's curator insight,
March 21, 2016 11:44 AM
An old Wired magazine article from 2012 that is still as current today as it was then. Unfortunately.
If you don't read the whole thing, just skip to the DOs and DONTs. And read these other articles: http://www.scoop.it/t/digital-transformation-of-businesses/?tag=Security 
jasmine moriah gabrielle hummel's curator insight,
April 6, 2016 7:40 PM
DON’T •Reuse passwords. . •Use a dictionary word as your password. •Use standard number substitutions. •Use a short password DO •Enable two-factor authentication when offered. •Give bogus answers to security questions. •Scrub your online presence. •Use a unique, secure email address for password recoveries

Farid Mheir's curator insight,
November 11, 2015 7:50 PM
I knew they did this for dogs but never thought they did it for humans. But come to think of it, makes perfect sense. Or it will become the biggest invasion of privacy ever. Great insight from André! 
Luigi Cappel's comment,
November 21, 2015 2:25 PM
For me it would depend on what part of the world I live in. In New Zealand I would have no problem wearing a chip that I could use for ID for building access, customs, instead of passwords or finger scanners. Being a law abiding citizen in a relatively corruption free country, I'd be more than happy, providing as per the law, I knew how any information about me was being used and could revoke access where it was abused. If I was living in other countries, which may remain nameless, I would steer well clear, because being innocent and law abiding doesn't mean that you are safe.

Farid Mheir's comment,
November 21, 2015 5:33 PM
@Russell R. Roberts, Jr. @Luigi Cappel both of you thank you for insightful comments and reshare... as always!

Farid Mheir's curator insight,
September 14, 2013 12:02 PM
I've been following collusion addon since its inception and I use it on a regular basis to remember all the digital breadcrums I leave behind as I roam around on the Internet. This is an awakening video but unfortunately the collusion software fail to offer us paths to minimize what behavioural tracking - aside from blocking all ads. |

Curated by Farid Mheir
Get every post weekly in your inbox by registering here: http://fmcs.digital/newsletter-signup/
|




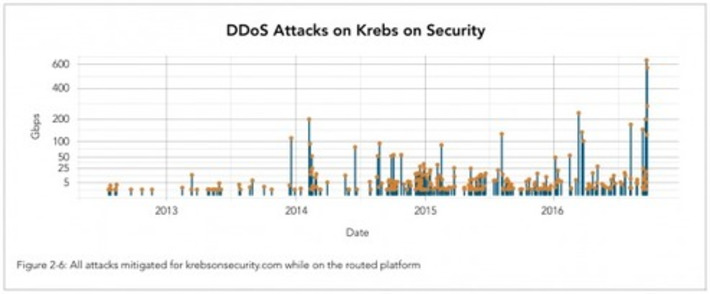


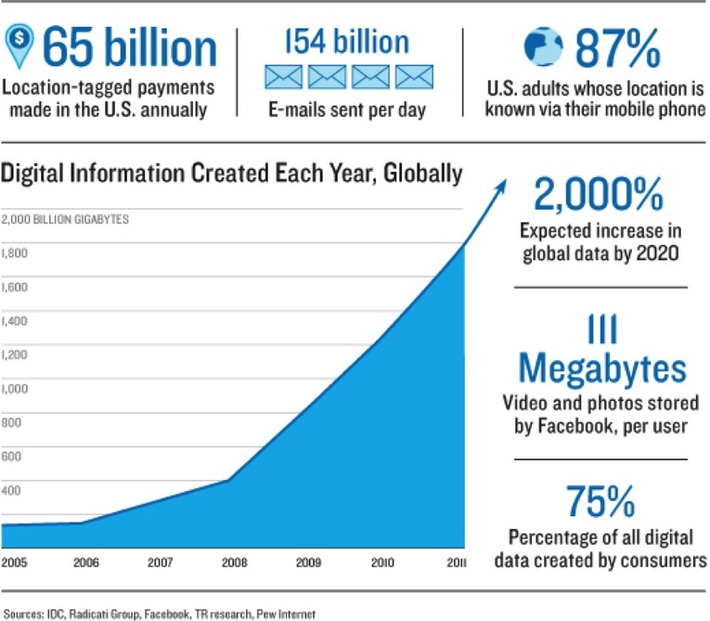








Describes recent DDoS attacks and provides links to Akamai State of the Internet report, a very useful reference.
WHY THIS IS IMPORTANT
Going digital often means relying on the Internet for critical business operations. This article is a stark reminder of the need to put security on the top of priority list.