 Your new post is loading...

|
Scooped by
Farid Mheir
|
Our tech columnist listened to four years of his Alexa archive, and discovered Amazon tracks us in more ways than we might want.

|
Scooped by
Farid Mheir
|
Our tech columnist offers some practical advice for fighting back against iOS apps hungry for your personal data.

|
Scooped by
Farid Mheir
|
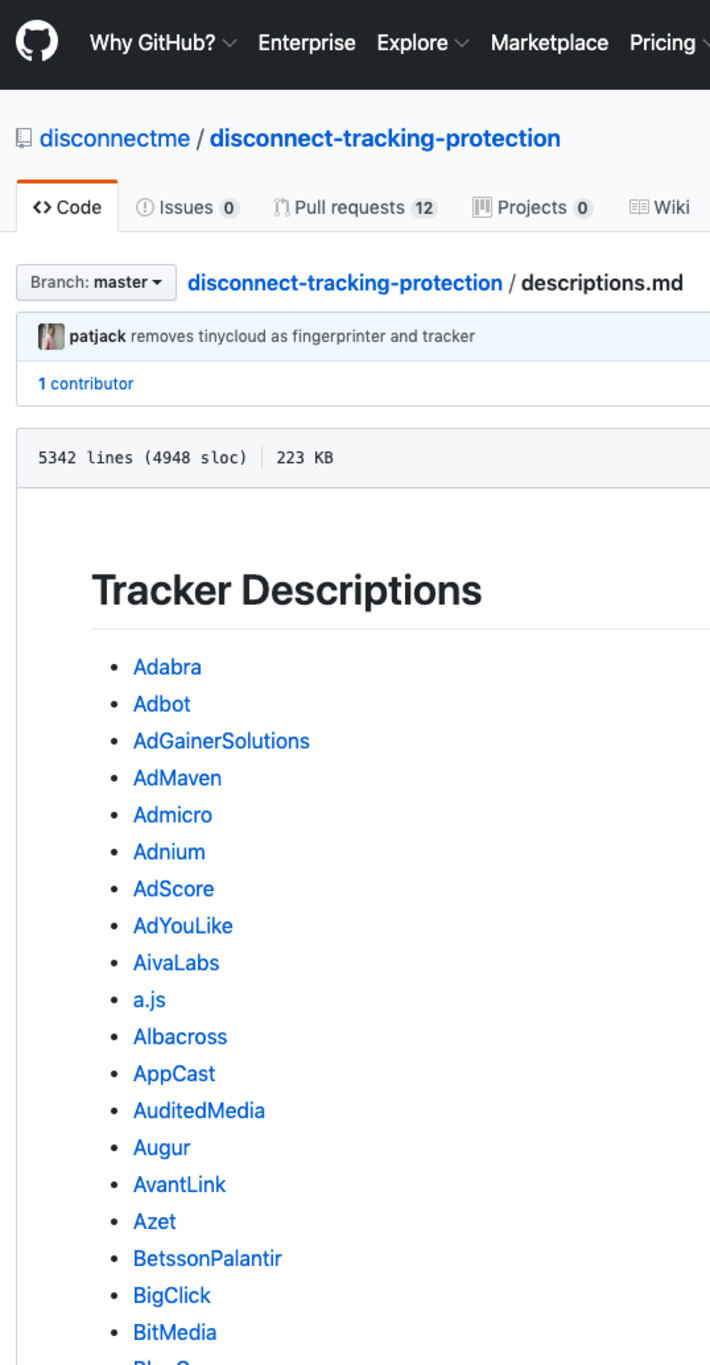
The open source list of trackers that powers our browser extensions, Firefox’s private browsing mode, and other popular privacy tools can be found here along with a change log and notes.

|
Scooped by
Farid Mheir
|
We ran a privacy experiment to see how many hidden trackers are running from the apps on our iPhone. The tally is astounding. Apple says, “What happens on your iPhone stays on your iPhone.” Our privacy experiment showed 5,400 hidden app trackers guzzled our data — in a single week.

|
Scooped by
Farid Mheir
|
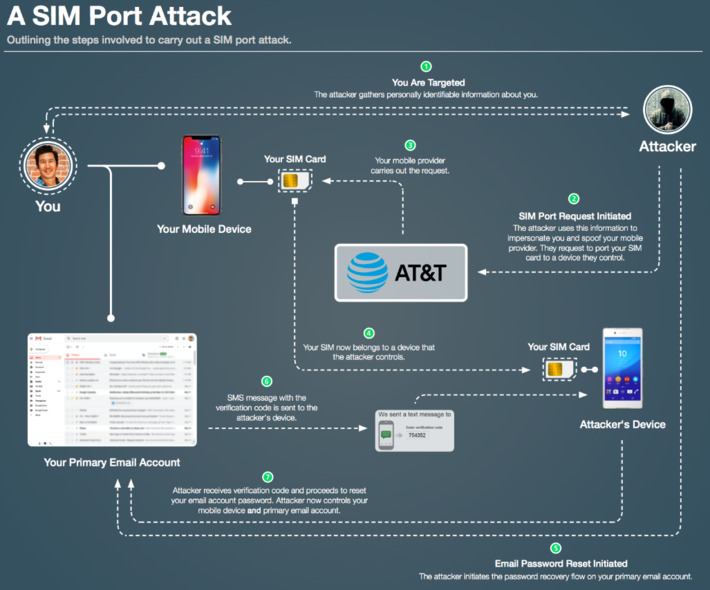
I lost north of $100,000 last Wednesday. It evaporated over a 24-hour time span in a “SIM port attack” that drained my Coinbase account. It has been four days since the incident…

|
Scooped by
Farid Mheir
|
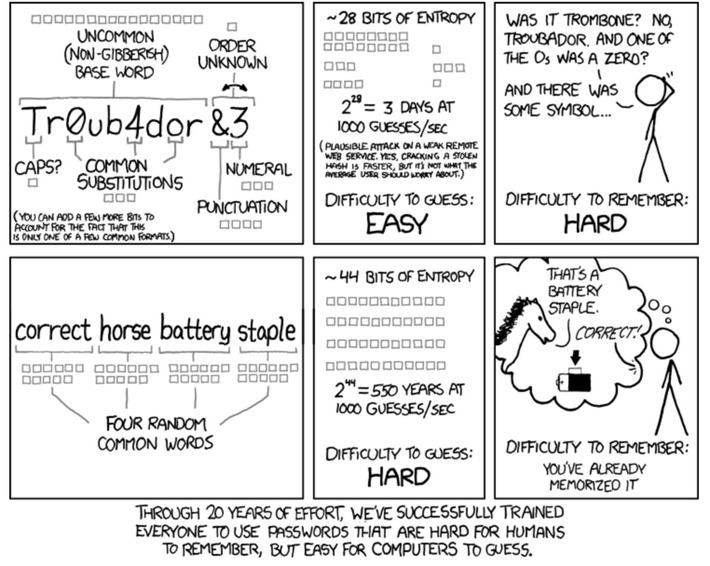
Passwords. We all have lots of them these days. And yet we're told repeatedly to not reuse passwords and to make them strong. For most of us, that's an opposing set of directives. Unless you have some amazing memory, there's no way that we mere mortal

|
Scooped by
Farid Mheir
|
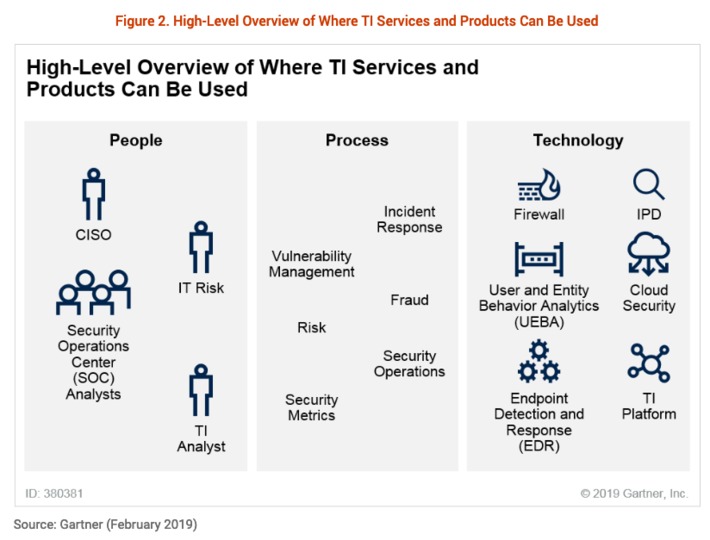
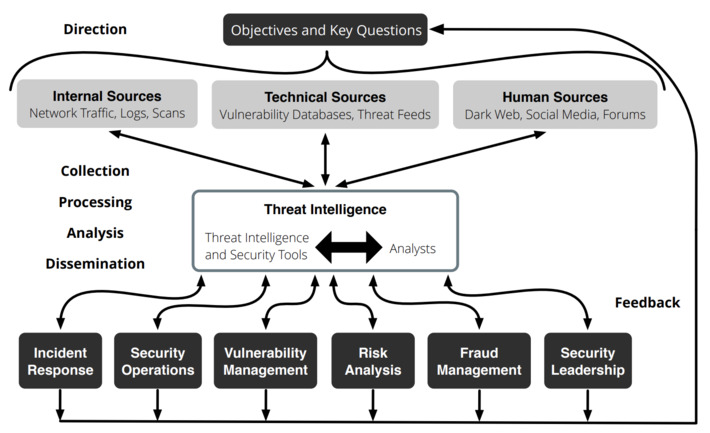
Market Guide for Security Threat Intelligence Products and Services. Key Findings:
- The term “threat intelligence” covers a diverse set of capabilities.
Client interest in industry-led government and commercial TI has increased significantly during the past two years. There are still large numbers of providers in this market, with startups also entering.
- The number and diversity of TI services, as well as expertise, have created an environment in which purchasers often struggle to compare services, and there’s still no single provider to address all of them. Many vendors can provide access to information; fewer provide truly anticipatory content or curation based on customized intelligence.
- The value of these services is sometimes constrained by the customer’s ability to afford, absorb, contextualize and, especially, use the information provided by the services.

|
Scooped by
Farid Mheir
|
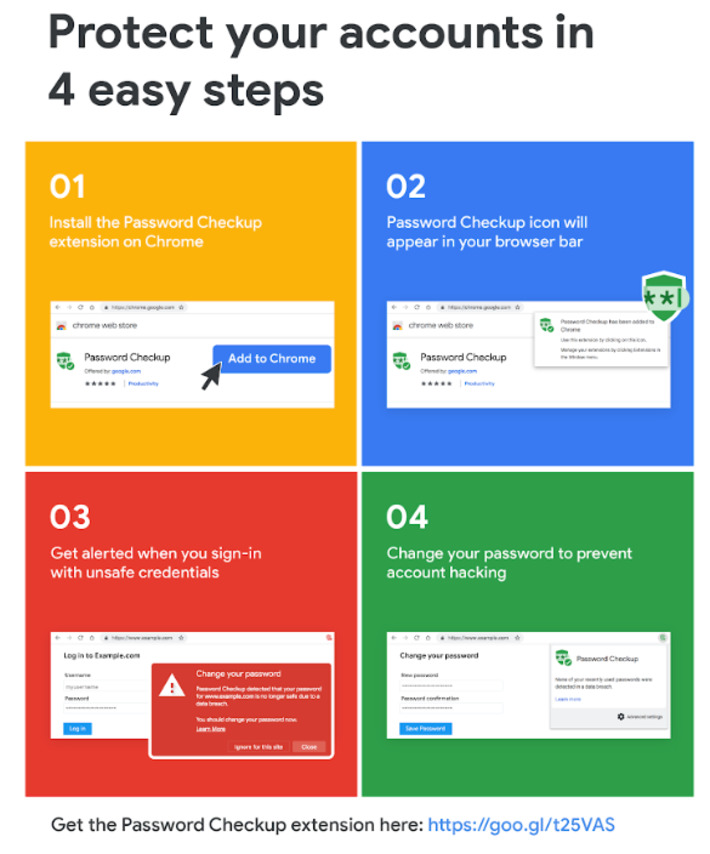
We’re rolling out two new features, Password Checkup and Cross Account Protection, to keep your information safe beyond Google’s sites and apps.

|
Scooped by
Farid Mheir
|
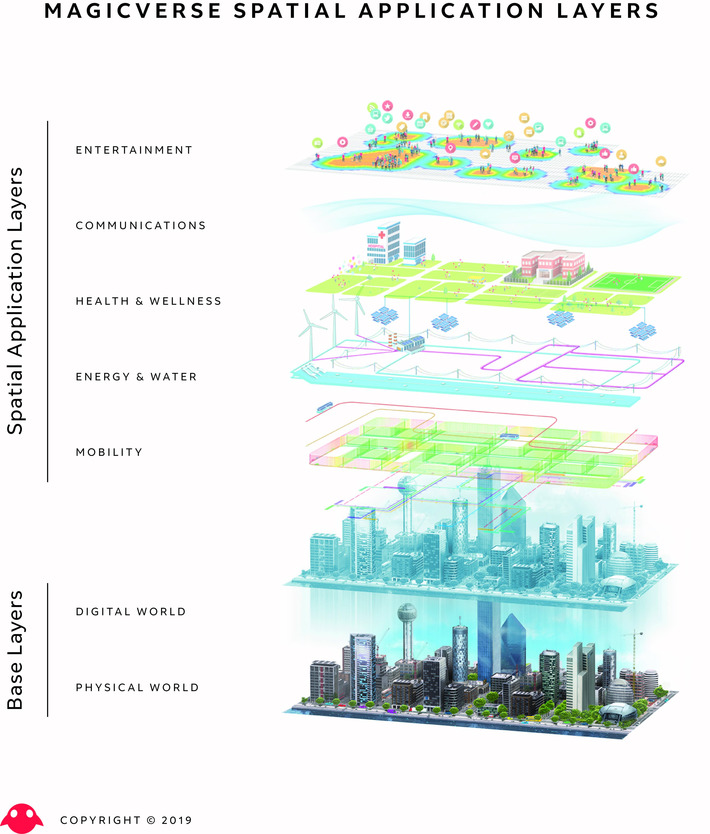
The Magicverse is an Emergent System of Systems bridging the physical with the digital, in a large scale, persistent manner within a community of people.

|
Scooped by
Farid Mheir
|
Last week brought an extraordinary demonstration of the dangers of operating a surveillance state — especially a shabby one, as China’s apparently is. An unsecured database exposed millions of records of Chinese Muslims being tracked via facial recognition — an ugly trifecta of prejudice, bureaucracy and incompetence.

|
Scooped by
Farid Mheir
|
Whether it was here on Hackaday or elsewhere on the Internet, you’ve surely heard more than a few cautionary tales about the “Internet of Things” by now. As it turns out, giving every gadget you own access to your personal information and Internet connection can lead to unintended consequences. Who knew, right? But if you need yet another example of why trusting your home appliances with your secrets is potentially a bad idea, [Limited Results] is here to make sure you spend the next few hours doubting your recent tech purchases.

|
Scooped by
Farid Mheir
|
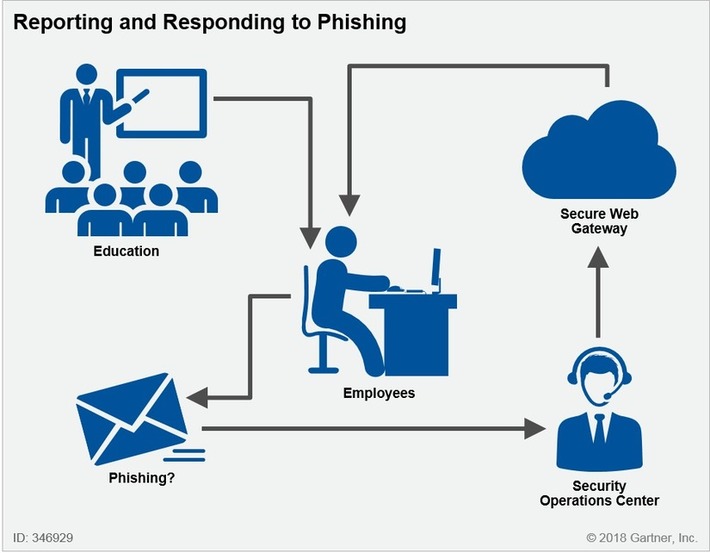
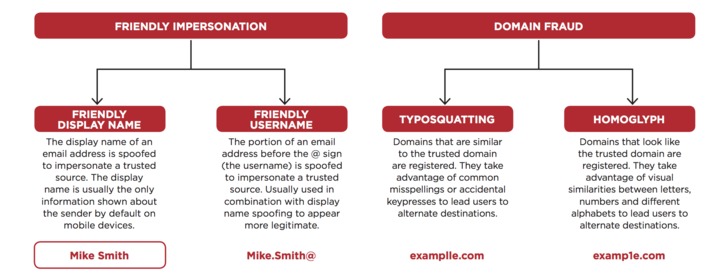
Phishing attacks are increasingly using impersonation to bypass traditional defense mechanisms. Weak sender identification will continue to present opportunities for creative attacks. Security and risk management leaders should use this research to adjust their strategy and business processes.
Key Challenges
Phishing attacks are still increasing as a targeting method of attackers. Phishing attacks targeting credentials will continue to escalate as applications and data migrate to better-protected cloud providers.
Email is not designed to truly authenticate sender identity. Efforts like DMARC to authenticate domains are not granular enough to authenticate users and do not address all attack types.
Most implemented secure email gateways (SEGs) are not designed with post-delivery detection and remediation techniques, costing incident responder and email admin time and reducing the feedback loop from end users.
User phishing education is a good start toward people-centric security, but current email security does not provide users with any indicators of the trust they can put in emails or the proper workflow for dealing with suspect emails.
Recommendations
Security and risk management leaders responsible for endpoint and mobile security should:
Upgrade secure email gateway solutions to cloud versions that include phishing protection, particularly for impostor or business email compromise (BEC) protection.
Integrate employees into the solution and build capabilities to detect and respond to suspect attacks.
Work with business managers to develop standard operating procedures for handling sensitive data and financial transactions.
Strategic Planning Assumptions
By 2023, sender identity verification will be a common critical component on secure email gateways and other anti-phishing solutions.
By 2023, anti-phishing education will be a critical part of the feedback loop between end users and email security solutions.
Through 2023, business compromise attacks will be persistent and evasive, leading to large financial fraud losses for enterprises and data breaches for healthcare and government organizations.

|
Scooped by
Farid Mheir
|
This infographic breaks down the chapters of our new handbook by security roles to show how each role can identify risks faster and more accurately.

|
Scooped by
Farid Mheir
|
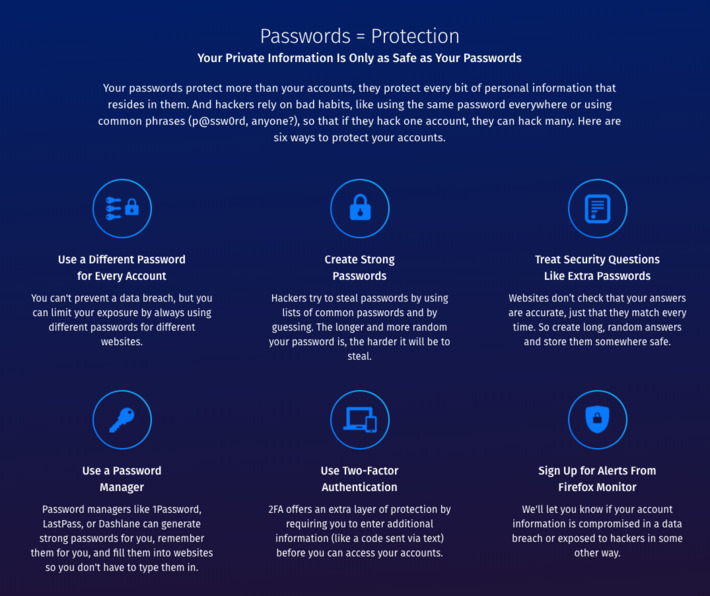
Passwords are awful. The software security industry expects us to remember 100+ passwords, that are complex (variations of upper & lowercase, numbers and special characters), that are supposed to be changed every 3 months, with each one being unique. Obviously this is impossible for most people, and for those whom it is possible, why would they want to waste all of that brain power on something that is, essentially, meaningless? *** This article is for beginners in security or other IT folk, not experts.

|
Scooped by
Farid Mheir
|
This article breaks down the best OSINT tools, techniques, resources and websites available online for every stage of intelligence gathering process. From background reading, to organizing your research and getting the best out of search engines, Intelligence Fusion has created the ultimate list of open source intelligence tools.
We cover the following;
What is OSINT?
The Best OSINT Websites for Background Reading
OSINT Techniques to Organise your Thoughts
Setting up Automated Alerts using OSINT Tools
OSINT Tools for Social Media
OSINT Techniques: Getting the Best out of Search Engines
Platforms and Dashboards for Open Source Intelligence
OSINT Websites for Online News Media
Other Useful OSINT Tools

|
Scooped by
Farid Mheir
|
Securitas 2018 investor update conference presents the strategy for the future.

|
Scooped by
Farid Mheir
|
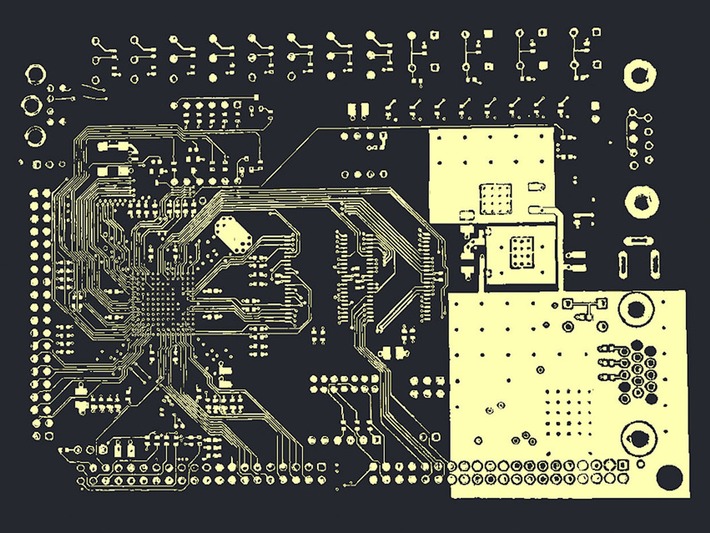
So why isn’t this system in widespread use? After all, much of it has been available since 2014. (Tehranipoor even described some in his 2017 article for IEEE Spectrum about the dangers of cloned chips.) “Sometimes a technology is ready, but it’s not used by companies because an attack hasn’t been seen to be real,” Tehranipoor says. This attack might be enough to change that perception, he says.

|
Scooped by
Farid Mheir
|
We use A.I. and robotics to create collaborative, end-to-end security solutions for service providers and end users.

|
Scooped by
Farid Mheir
|
Have your accounts been leaked or stolen in a data breach? Find out at Firefox Monitor. Search our database and sign up for alerts.

|
Scooped by
Farid Mheir
|
As the point of entry for 91% of cyber attacks, email is every organization’s biggest vulnerability. From malware to malware-less attacks including impersonation attacks like CEO fraud, a single malicious email can cause significant brand damage and financial losses. Understanding these ever evolving attacks and identifying the tactics used, is key to staying one step ahead of cyber criminals.

|
Scooped by
Farid Mheir
|
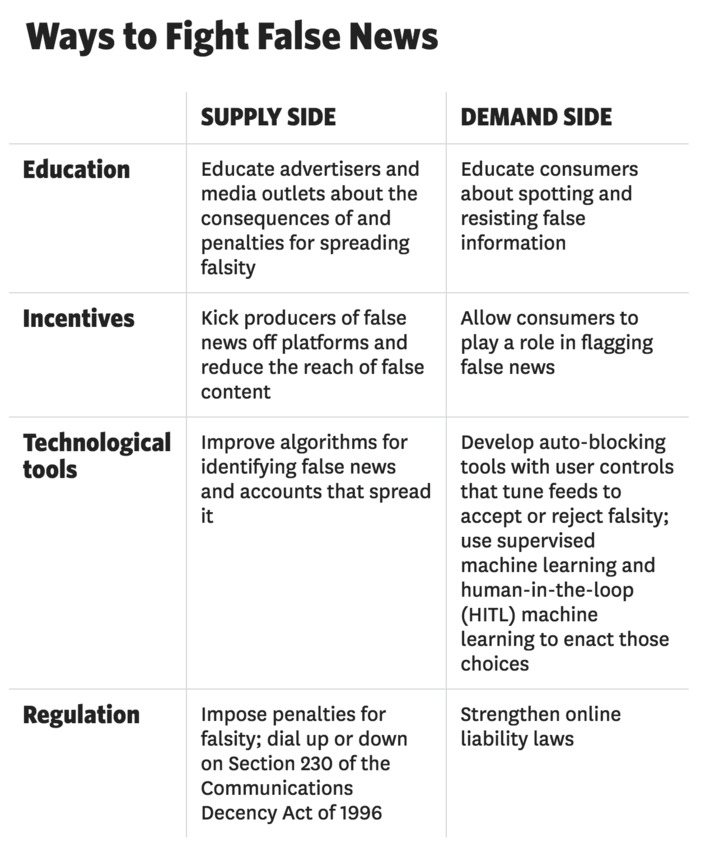
False news spreads online faster, farther, and deeper than truth does — but it can be contained. Here’s how.

|
Scooped by
Farid Mheir
|
The most common forms of 2FA require the user to supplement a password with a one-time code sent to their mobile device via text message or an app. Indeed, prior to 2017 Google employees also relied on one-time codes generated by a mobile app — Google Authenticator.
In contrast, a Security Key implements a form of multi-factor authentication known as Universal 2nd Factor (U2F), which allows the user to complete the login process simply by inserting the USB device and pressing a button on the device. The key works without the need for any special software drivers.

|
Scooped by
Farid Mheir
|
You’re surrounded by disruption and rapid change. Maybe you’re looking for solutions. A way to seize opportunities. We all are. It’s a sprint to stay ahead of technology. Blockchain. Automation. AI. Cybersecurity. It will forever change the way accounting is done. And forever change those who do it. It’s time to reset, redefine and reskill. The way we learn. The way we work. And the way we move forward. Here, you’ll find what you need to not just survive, but adapt and thrive. And disrupt disruption.

|
Scooped by
Farid Mheir
|
We live in a data-driven world. Almost every transaction and interaction you have with most organisations involves you sharing personal data, such as your name, address and birth date. You share data online too, every time you visit a website, search for or buy something, use social media or send an email.

|
Scooped by
Farid Mheir
|
Many people, particularly older folks, proudly declare they avoid using the Web to manage various accounts tied to their personal and financial data — including everything from utilities and mobile phones to retirement benefits and online banking services. The reasoning behind this strategy is as simple as it is alluring: What’s not put online can’t be hacked. But increasingly, adherents to this mantra are finding out the hard way that if you don’t plant your flag online, fraudsters and identity thieves may do it for you.
|

Curated by Farid Mheir
Get every post weekly in your inbox by registering here: http://fmcs.digital/newsletter-signup/
|
 Your new post is loading...
Your new post is loading...




































From the beginning I knew that G is Big Brother.