Worried about new ransomware attacks infecting your systems? Learn how ransomware works + get tips to block ransomware and deal with ransomware recovery.
Research and publish the best content.
Get Started for FREE
Sign up with Facebook Sign up with X
I don't have a Facebook or a X account
Already have an account: Login
Get weekly or monthly digest of all posts in your inbox: https://fmcs.digital/wim-subscribe
Curated by
Farid Mheir
 Your new post is loading... Your new post is loading...

Jean-Marie Grange's comment,
December 20, 2016 1:12 PM
Maybe one solution would be for content publishers to offer the choice of paying a fair amount for ad-free content... http://sco.lt/7CrAVl
Tracy Harding's comment,
September 1, 2015 9:19 AM
You need to work on formatting of your replies. This is one giant sentence. Remember the requirements. You need a 2-3 sentence summary, at least 1 sentence of IR implications and 1 sentence about your thoughts.

Farid Mheir's comment,
September 1, 2015 9:23 AM
@Tracy Harding: not sure I understand your comment re: formatting. Can you be more specific and email me a screengrab? thank you!

Peter Azzopardi's curator insight,
April 18, 2014 6:54 PM
Homomorphic encryption allows data to be processed in an encrypted form so that only the end user can access it in a readable form. So far it has been too demanding for normal computers to handle.

Farid Mheir's curator insight,
September 14, 2013 12:02 PM
I've been following collusion addon since its inception and I use it on a regular basis to remember all the digital breadcrums I leave behind as I roam around on the Internet. This is an awakening video but unfortunately the collusion software fail to offer us paths to minimize what behavioural tracking - aside from blocking all ads. |

Curated by Farid Mheir
Get every post weekly in your inbox by registering here: http://fmcs.digital/newsletter-signup/
|




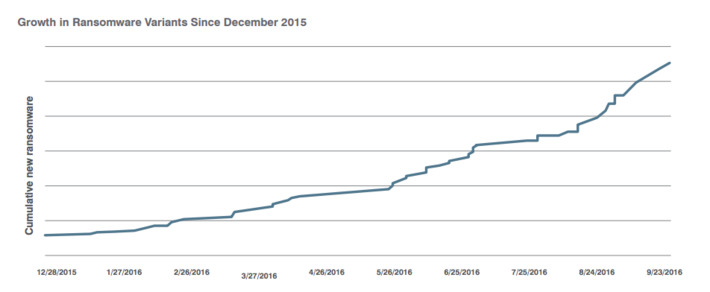


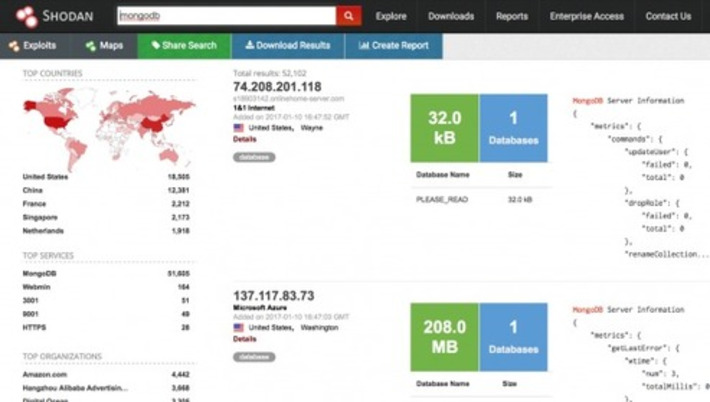
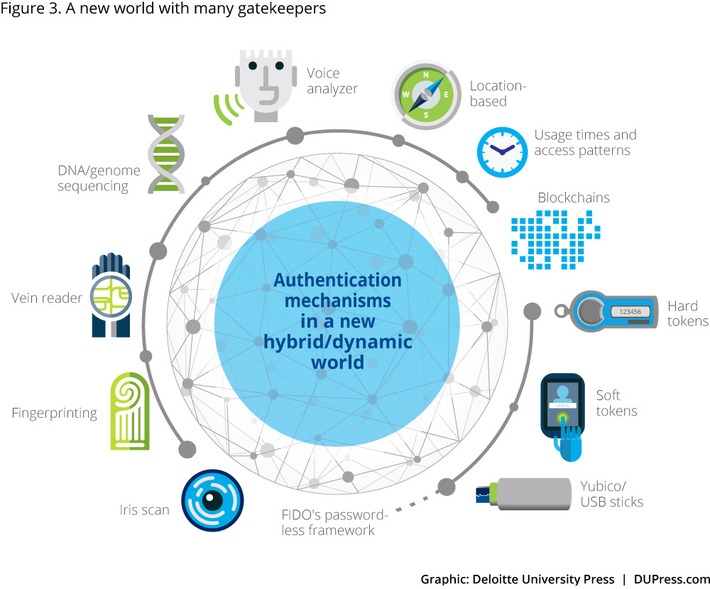


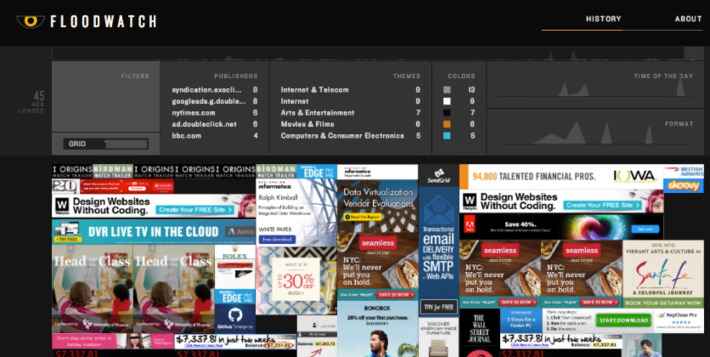
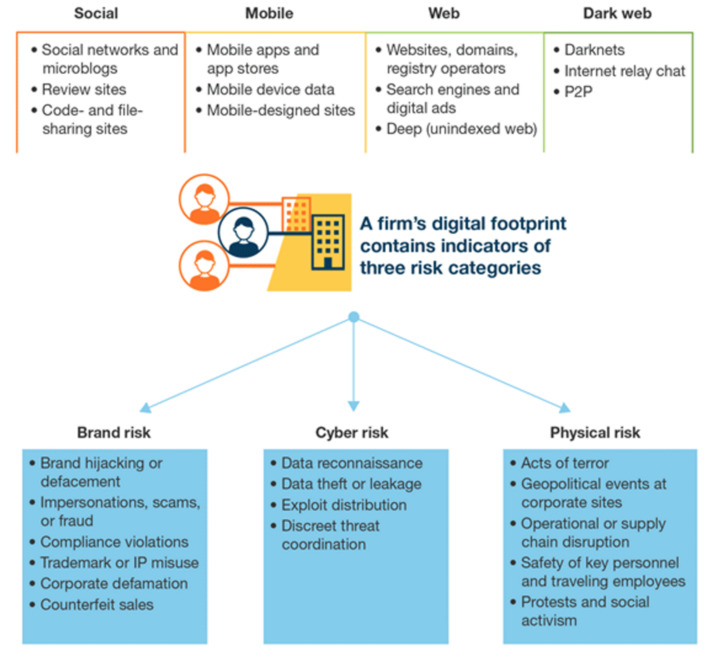
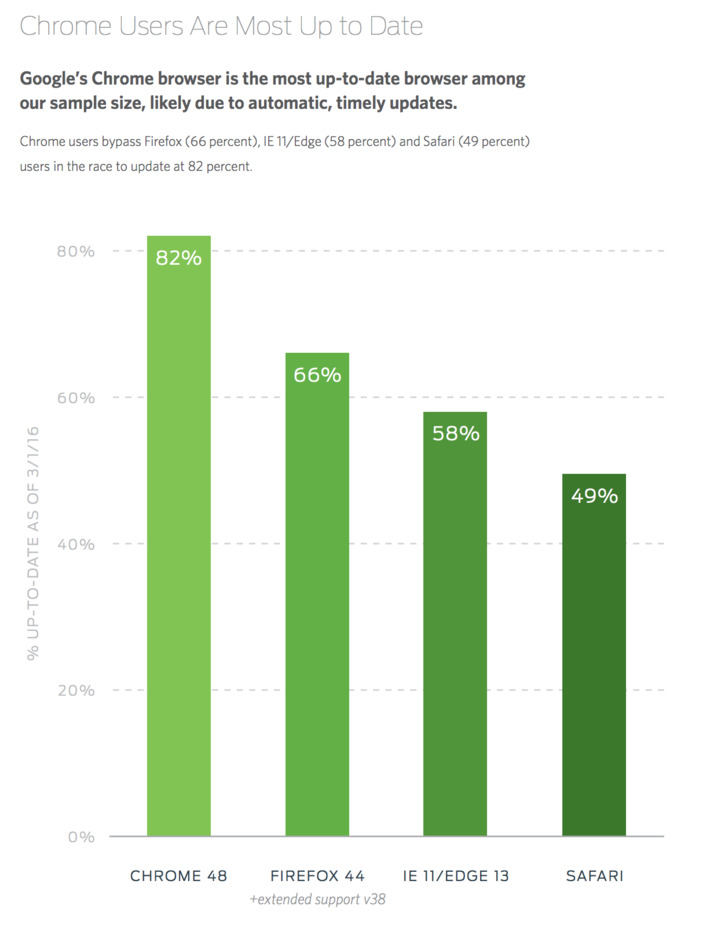
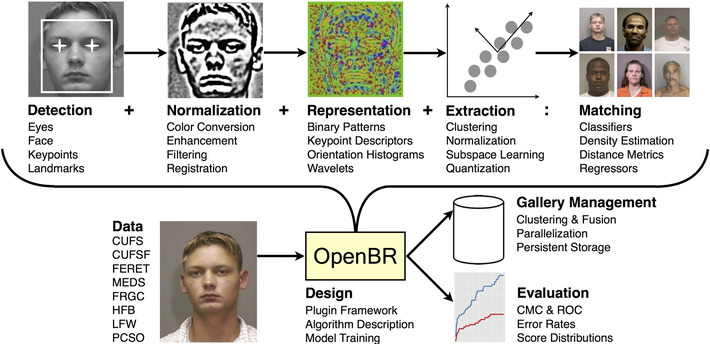


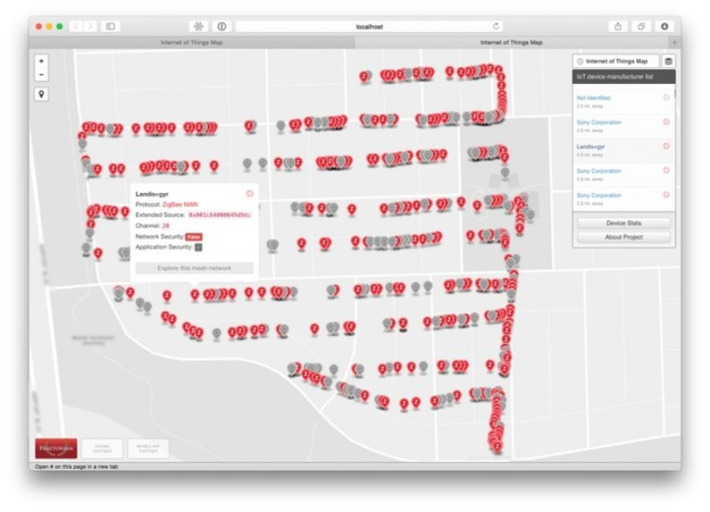











Amazing reference concerning ransomware: what they are, trends, recommendations, etc. Very well done, very useful.