Anonymous data sets are an enormous boon for researchers, but the recent de-anonymization of Netflix customer data shows there are privacy risks as well. Commentary by Bruce Schneier.
Research and publish the best content.
Get Started for FREE
Sign up with Facebook Sign up with X
I don't have a Facebook or a X account
Already have an account: Login
Get weekly or monthly digest of all posts in your inbox: https://fmcs.digital/wim-subscribe
Curated by
Farid Mheir
 Your new post is loading... Your new post is loading...

Maria Ioia's curator insight,
March 8, 2015 8:57 PM
I thought smart phone biometrics was interesting. This is ridiculous!

Peter Azzopardi's curator insight,
April 18, 2014 6:54 PM
Homomorphic encryption allows data to be processed in an encrypted form so that only the end user can access it in a readable form. So far it has been too demanding for normal computers to handle. |

Curated by Farid Mheir
Get every post weekly in your inbox by registering here: http://fmcs.digital/newsletter-signup/
|












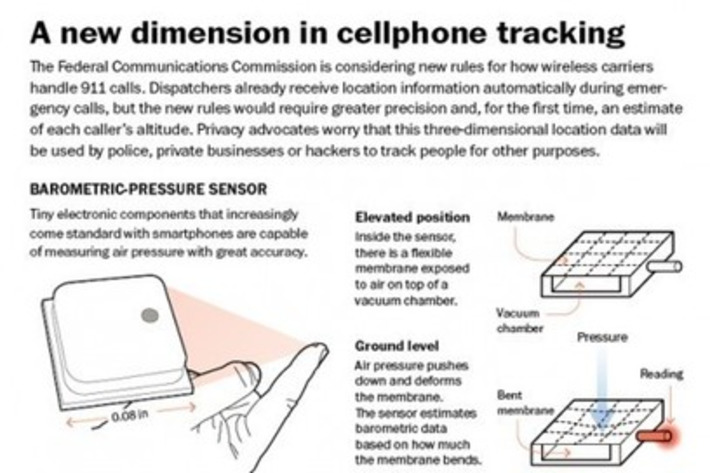





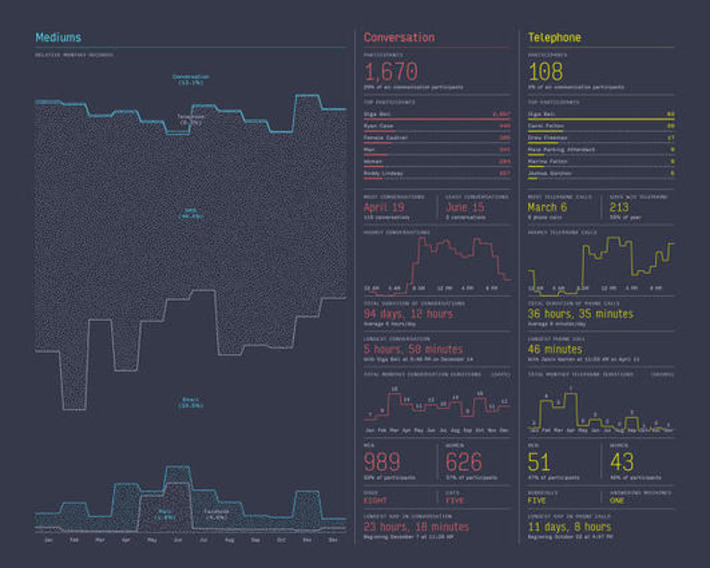



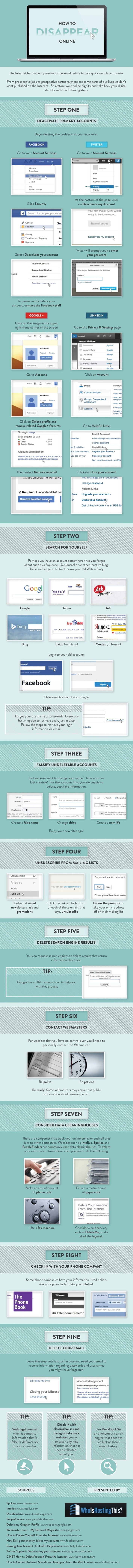


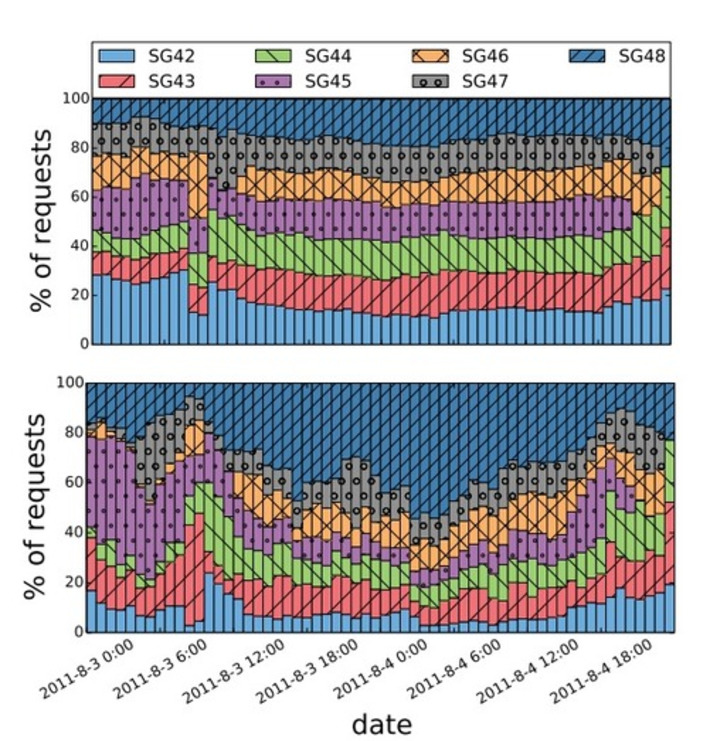

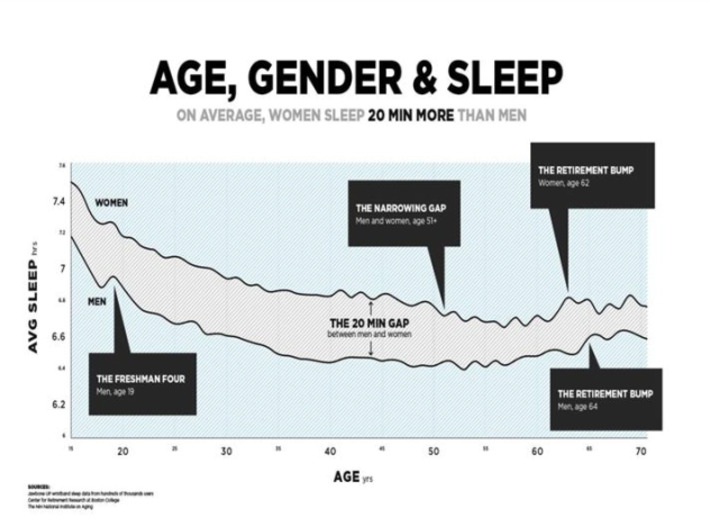









Even anonymous data can be used to identify you, when coupled with other information.