The nation's hacker-in-chief took up the ironic task at the Enigma Conference in San Francisco.
“We put the time in …to know [that network] better than the people who designed it and the people who are securing it,” he said. “You know the technologies you intended to use in that network. We know the technologies that are actually in use in that network. Subtle difference. You’d be surprised about the things that are running on a network vs. the things that you think are supposed to be there.”



 Your new post is loading...
Your new post is loading...




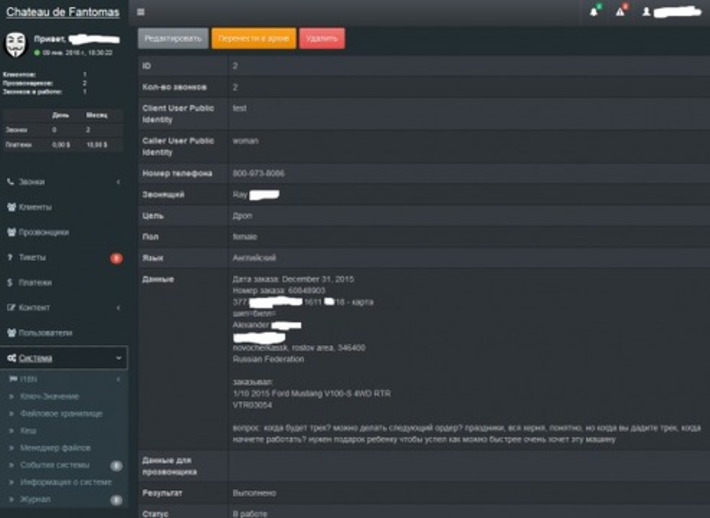


























Excellent article and video from NSA chief on hacking network security. Hackers will spend the time to understand a network and its vulnerabilities. Something most companies don't.
And I believe it. Security, to be effective, requires a lot of time and effort, which most companies are not willing to invest - because it is for prevention and thus may appear to be an unnecessary cost if there are no security breaches!
Moreover, applying the security best practices that are presented here mean that access to network is difficult, requires special tools and software, prevents users from bringing their devices to work, etc. So it is actually very annoying for users to have secure networks. Thus, users will find ways to bypass it by using cloud solutions or installing shadow IT solutions.
If you feel technically inclined and want to investigate further, read wikipedia entry on packet injection and head out to airpwn for a simple tool that will make you never trust an open wifi connection (Startbucks free wifi anyone) in the future...
https://en.wikipedia.org/wiki/Packet_injection
http://airpwn.sourceforge.net/Airpwn.html
Credits to La Sphere, Radio Canada's very good weekly show on all things web and digital.